CRSF, cross site request forgery
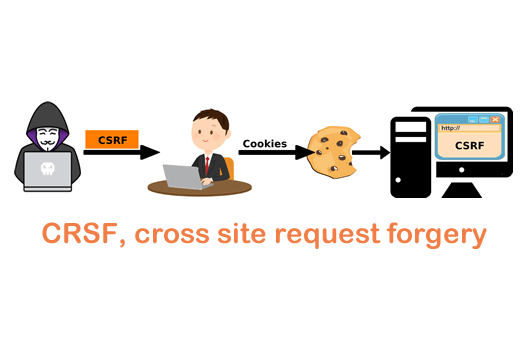
Cross-Site Request Forgery (CSRF) is a type of cyber attack that involves tricking a user into making unintended actions on a website. These actions can include things like changing the user's password, transferring money, or deleting data. CSRF attacks are often executed by an attacker through the use of maliciously crafted links or web pages.
In a CSRF attack, the attacker exploits the trust that a website has in a user's web browser. When a user logs in to a website, the website stores a cookie in the user's web browser to keep track of the user's session. This cookie allows the website to recognize the user whenever they make requests to the website, even if they are coming from different web pages.
An attacker can exploit this trust by sending a malicious link or web page to a user. When the user clicks on the link or visits the web page, their web browser will automatically send the cookie stored by the website to the attacker's website. The attacker can then use this cookie to make requests to the website on behalf of the user, allowing them to perform unintended actions.
To protect against CSRF attacks, it is important for websites to implement a defense mechanism known as a CSRF token. A CSRF token is a unique, randomly generated value that is associated with each user's session. When a user makes a request to the website, the website checks the CSRF token to ensure that the request is legitimate. If the CSRF token is missing or invalid, the website will reject the request.
In summary, CSRF is a type of cyber attack that involves tricking a user into making unintended actions on a website. To protect against CSRF attacks, websites should implement a defense mechanism such as a CSRF token to verify the legitimacy of user requests.

